Efficient next-generation cybersecurity
Radar Services comprises everything relating to hardware, software and expert know-how. Highly trained experts at the Cyber Defense Center use cutting-edge technology to manage risk identification processes. Companies can see the current IT security status in their organization at the push of a button, enabling them to take timely action with the support of our experts.
SOC as a Service
Radar Cyber Security sets up a Cyber Defense Center (CDC), also called Security Operations Center (SOC), in your company and manages its continuous operation. Quickly up and running, using tried and tested principles and based on cutting-edge technology developed in Europe. Personal contact in your local language, clear rules and documented processes for structured procedures and easy communication with your company. Choose your ideal service hours, including incident response and real-time alerting.
Radar Cyber Defense Center provides all tools and manages the continuous operations. Choose risk detection modules that are tailored to your needs and that come with expert analysis by our Risk & Security Intelligence Team in real time, daily, weekly or monthly intervals.
IT Security Monitoring
The increasing interconnection of IT systems leads to new vulnerabilities for attacks from both the inside and outside. Continuous and central IT Security Monitoring of the IT infrastructure and its components is essential. Radar Cyber Security continuously monitors the entire IT infrastructure and applications and evaluates all data results, specifically searches for weaknesses in systems and their configuration and intelligently analyses the network traffic.
Your benefits
State-of-the-art European technology
Comprehensive integrated solution
Highly trained experts and continuously updated threat intelligence
Tailor-made solution and established analysis processes
Reduction in operating and maintenance costs
Radar Risk & Security Cockpit with current overview of IT risks including real-time warning
Flexible and scalable solution
Complying with EU General Data Protection Regulation (GDPR)
Know what is really important
Around-the-clock automated IT security monitoring and risk detection
Customer-specific requirements mapped as detection scenarios
Analysis conducted by the Risk & Security Intelligence team
Automated Radar reports at predefined intervals
System configuration and alert function
Asset and user management
Pentesting on demand
Your results
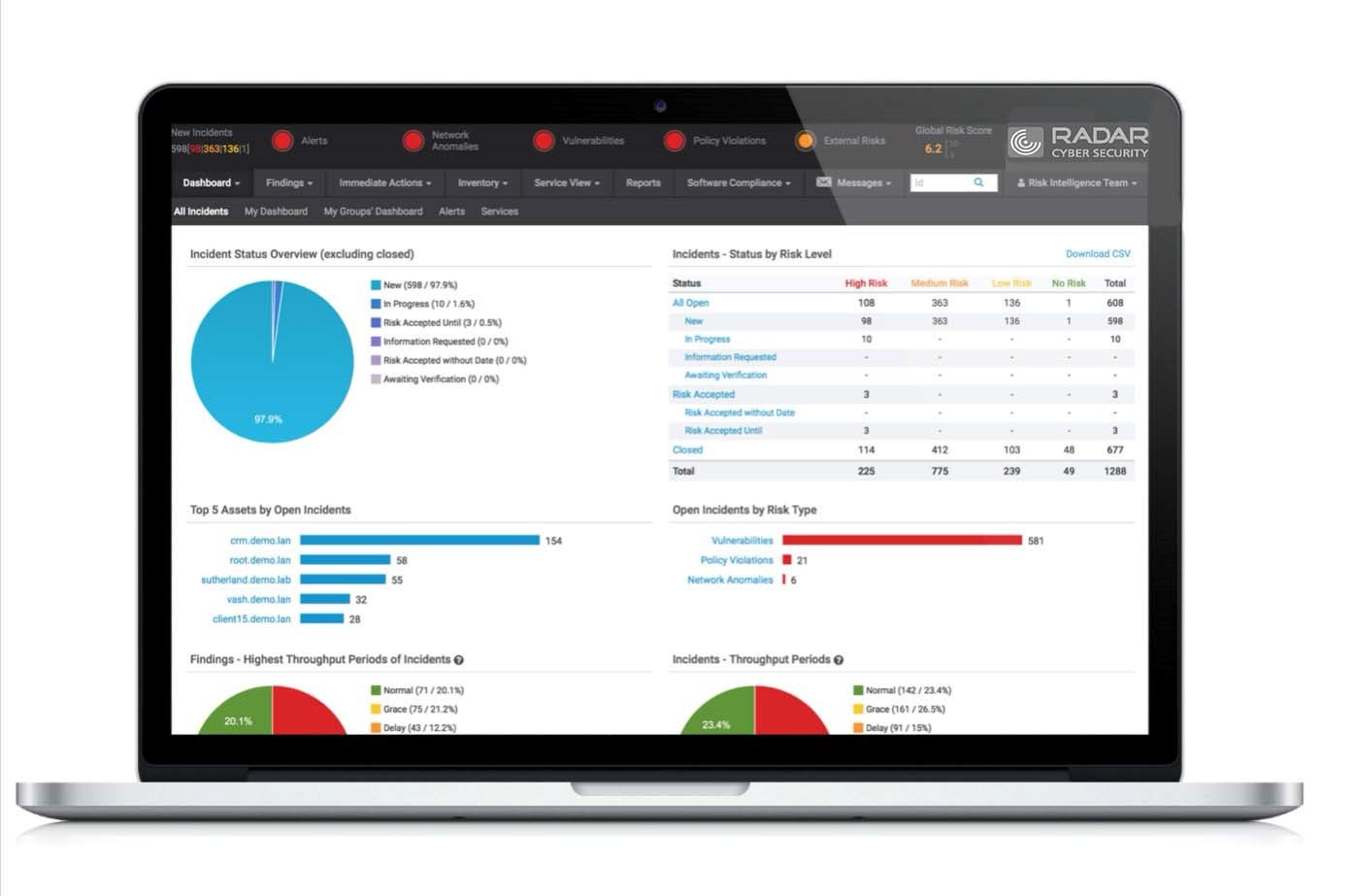
All IT risk and security information centrally presented in the Risk & Security Cockpit.
Customized risk reports at the press of a button
Real-time alerts are triggered by means of dynamic threshold values
Developing customer-specific detection scenarios being gradually assumed by the Risk & Security Intelligence team
Structured IT risk management process ensures a high degree of transparency
The path towards more IT and OT security
Radar Services
with LDA and NBA*
*available On Premise and Cloud
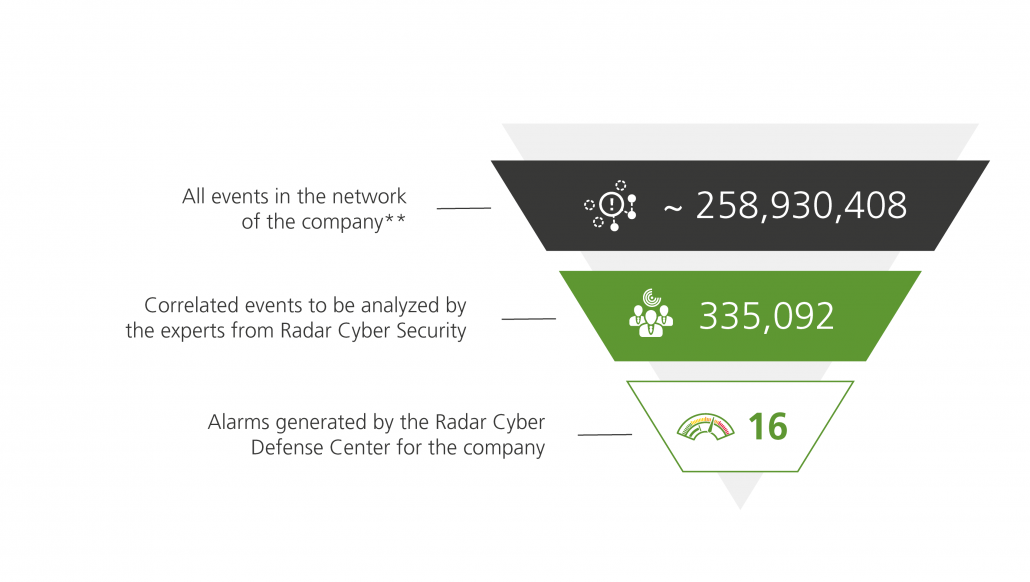
**Values refer to the monthly average of one customer (> 10,000 employees) in 2019
Professional cyberdefense
Our ability to successfully combine technologies and expertise is what enables us to stand out from the rest. The risk detection IT module, together with the Advanced Correlation Engine, Big Data Analytics, Threat intelligence and Machine Learning, along with the experience of the Cyber Defense Center analysts round off our cyber security package.
The growing number of devices means that the number of potential access points is also on the rise. It is possible to automatically analyze a large portion of these in advance by using the modules and then correlating the data. The cyber security experts consider the context of security-relevant data and evaluate incidents.
This consolidated and verified IT risk and security information is provided to customers in a clear way for remedial action to be taken, thereby significantly reducing the time from when the problem is detected to when it is reacted to and a solution found.
Risk & Security Cockpit
All IT risk and security information is presented centrally in the Risk & Security Cockpit. Customized risk reports and statistics are easy to understand and are available at the press of a button. Real-time alerts are triggered by means of dynamic threshold values. Our Manager Services offer involves experts gradually assuming responsibility for further developing customer-specific detection scenarios.
Radar Cyber Security keeps an eye on incidents in public institutions, critical infrastructure, the automotive industry, manufacturing, utility companies, and in banking and financial institutions.
IT security is more than SIEM
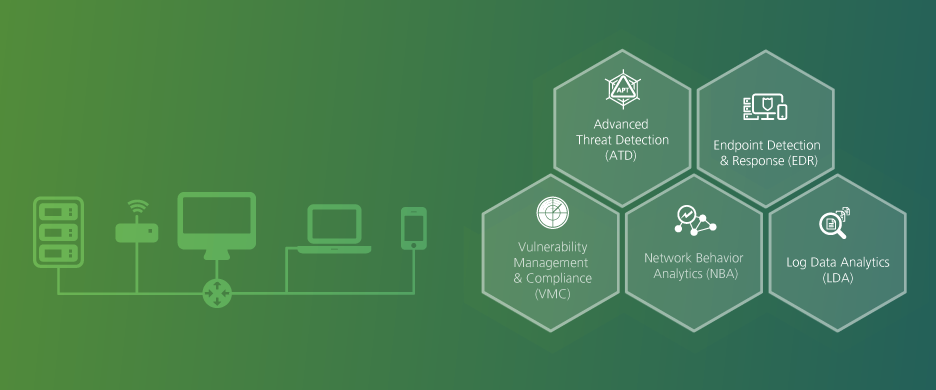
Comprehensive IT security monitoring becomes reality with our IT Detection Modules, that are able to identify nascent IT risks. The Radar Cyber Defense Center currently works with 5 modules:
Log Data Analytics (LDA)
Log Data Analytics, also known as Security Information and Event Management (SIEM), comprehends the collection, analysis and correlation of logs from various sources, distributing alerts in case of security flaws or potential risks.
Network Behavior Analytics (NBA)
With Network Behavior Analytics we detect malware, anomalies and other risks in network traffic, deriving from signature and behavior-driven engines.
Vulnerability Management & Compliance (VMC)
Vulnerability Management and Compliance enables consistent internal and external vulnerability scans with comprehensive detection, compliance checks and coverage tests. As part of an integrated software compliance check, authorized/unauthorized software is determined for each server or server group using a set of rules and a continuous analysis pattern of the current status.
Advanced Threat Detection (ATD)
Advanced Cyber Threat Detection consists of sandbox technologies of the latest generation, that detect advanced malware throughout emails and downloads. Suspicious email traffic will be alarmed and flagged.
Endpoint Detection & Response (EDR)
Endpoint Detection and Response enables analysis, monitoring and detection of host anomalies, leading to active reactions and immediate alarms.
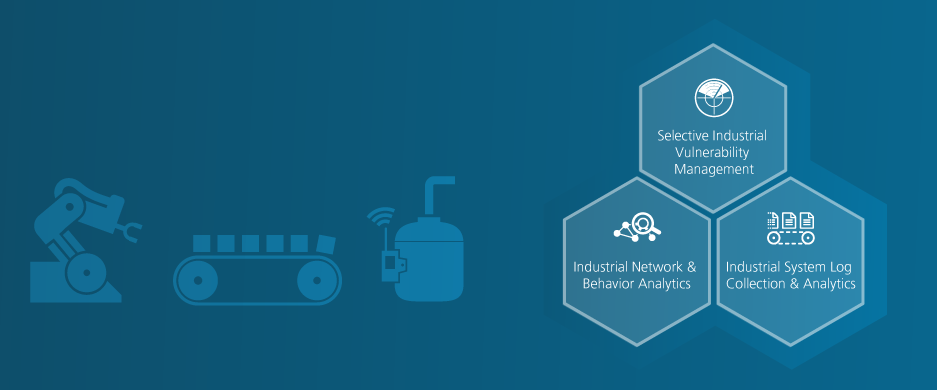
Closing OT security gaps
Industrial networks connect the virtual with the physical world and thus represent critical goals. OT environments often consist of older and sensitive systems that are not adequately protected with security solutions. By networking IT and OT systems, there are new gateways for attackers from inside and outside.
Radar Cyber Security helps companies protect both IT and OT systems without interfering with work processes. OT Security Monitoring enables complete transparency of network traffic. This enables a better understanding and deeper insight into the underlying processes and leads to more security overall
Overview of OT Monitoring services
Analysis of OT command behavior
Continuous and passive scanning of the devices
OT honeypot to catch attackers
Automatic notification of security-related incidents
Real-time visualization of devices and their connections
Detecting and extracting information from various industry protocols
Location support
Flexible combination with further Radar Cyber Security services
Detailed visualization of devices and collected knowledge
Safeguarding tomorrow’s manufacturing
Increasing interconnectedness of OT systems leads to new vulnerabilities for attacks from both the inside and outside. Continuous and central OT Security Monitoring of the OT infrastructure and its components is essential. Radar Cyber Security continuously monitors the entire OT infrastructure and applications and evaluates all data results, specifically searches for weaknesses in systems and their configuration and intelligently analyses the network traffic.