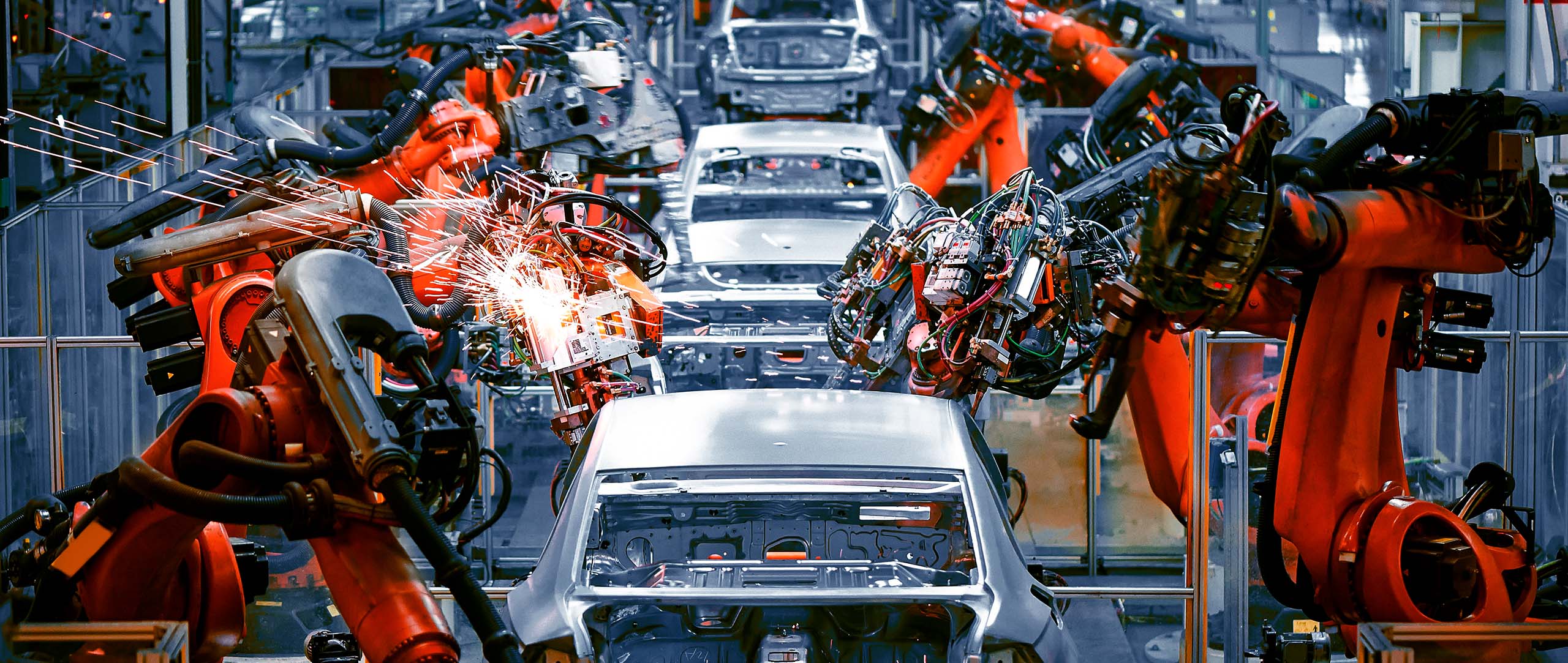
The risks and sideeffects of digitization: Securing and protecting Industry 4.0
IT and OT systems are the foundation of the modern business world, connecting companies, institutions, societies, and economies with each other. Machines and robots are at work around the clock and are networked to a very high degree – both with each other and with the company’s IT system. For industrial companies, it is of particularly high importance to have protective mechanisms in place for what is known as operation technology (OT). Ensuring security in OT is subject to a very special set of framework conditions. The primary focus here is on non-stop operations: 24 hours a day, seven days a week, 365 days a year. Any actions taken occur in real time, which makes it difficult or even impossible to make any changes to the systems. There is also the fact that hardware and software are used for comparably long periods in production, in stark contrast to other applications.
Attacks on production operations can have serious consequences. For example, an aircraft manufacturer was forced to stop production for over a week. A global, publicly listed aluminum producer had to pay an estimated EUR 64.9 million to restore operations after a cyber attack using ransomware, not counting the loss of production and earnings, which came to over 80 percent.
Disarming cyber safecrackers
Cyber attacks and incidents of this kind make it quite clear that what is needed is a holistic, well thought-out security concept that includes both OT and IT. The digitization and interconnectedness of IT and OT open the door for attackers to cause damage in both settings.
IT systems used by financial services companies need to meet the highest demands in terms of speed and availability and are an essential part of ensuring smooth operations.
The complex core banking systems as well as online or mobile banking are focal points for IT security at banks. Another focus is on securing branch operations and helping analyze large amounts of data.
Financial services providers have an ever-growing responsibility to ensure IT security and privacy not least in view of the number of large-scale attacks, fake emails, and websites, as well as the publication of bank details and credit card information in recent times. Immense financial damage is caused by data being stolen or surreptitiously changed, along with substantial reputational damage to the targeted institutions.
On the safe side
The security monitoring process encompasses all systems and data traffic, along with access to sensitive systems and files, to ensure the integrity of the financial systems. In addition to network behavior analysis, other modules are also used to detect data transfers from internal to external IP addresses with which no business relationship exists. Log data from servers, network devices, and applications are also analyzed centrally and the findings correlated.
This is the only way to detect attacks that have a negative impact on your company or target your customers in a timely way.
The Radar Risk Cockpit is where critical information from security monitoring and risk assessments are displayed so that immediate corrective action can be taken.
Energy suppliers are part of the critical infrastructure sector, which means they are subject to special security requirements.
The high degree of complexity of the IT and OT systems used and the complex network of relationships that facilitate the multidimensional exchange of information between the parties present new opportunities for potential risks. The confidentiality and protection of personal data relating to private households is of paramount importance in addition to ensuring the availability and integrity of the entire OT and IT systems, networks, measuring devices, and components.
The complexity of how different actors work together, the structures of IT and OT systems, and the diverse functionalities and direct control options offer cyber attackers numerous potential entry points.
The types of threats are manifold and range from attacks with financial or sabotage-related motives, malware, zero-day attacks, botnets, denial of service, and distributed denial of service, through to complex advanced persistent threats that could be deployed in a targeted way to take control of PC workstations from staff working in smart metering settings.
Smart protection
Radar Cyber Security’s IT and OT Security Monitoring service detects critical events in the network at various different levels. The Security Intelligence Team and the customer’s security team receive a report on these events. Radar Cyber Security’s Security Intelligence Team immediately analyzes the events and guides the customer through the process of eliminating the risks.
For example, Radar Cyber Security identifies SCADA command packets within the SCADA network of an energy company that arrive at sensitive control systems in excessive numbers. As soon as a defined threshold value is exceeded, alerts are triggered which enable the customer’s monitoring team to intervene before SCADA control systems crash.
Customer web portal
Access to customer data and database
Smart meter control
Access to the entire power system and shutting down of the power supply
Protocols and control systems
Destabilization of smart meters or attack on other accessible IT and OT systems
PC workstations used to manage smart meters
Penetration of core smart metering systems paired with blackmailing
PC workstations of the SCADA systems
SCADA systems administrators are incapacitated by malware. Attempts are made to manipulate SCADA systems.
Infiltration of foreign devices
If infectious foreign devices are connected, malware can be distributed unhindered and cause damage
The more networked vehicles are, the more vulnerable they become. After all, more software, functionalities and interfaces installed in the car automatically translates into more scope for cyber attacks. The rising degree of automation and modern vehicle functions must be protected by security measures. This has an impact on comfort such as entertainment and navigation systems and, more importantly, an impact on road safety, which increases with the use of driver assistance systems, semi-autonomous or autonomous driving.
The car manufacturers themselves must also be protected in addition to car remote controls and applications in cars that communicate constantly with each other. Given that vehicles communicate and transmit information to the outside world via interfaces, servers and infrastructures that collect and process such data must be properly protected.
Protecting mobile data centers
For these reasons, comprehensive security concepts are needed that offer comprehensive protection for vehicles, connected systems, and customer end devices. Vehicle and user data must be protected against unauthorized access and external manipulation. Automotive security looks after the privacy concerns of customers as well as the security of the vehicle and its functions with all the components that have been installed. In doing so, the highest cyber security standards must be ensured to maintain regulated road traffic and to protect vehicles and passengers.
Early detection is the safest way to prevent hackers and data thieves. Network, log data analysis, vulnerability management, and other detection modules serve as additional support here. The Radar Risk Cockpit provides the essential information and summaries to enable risks to be eliminated immediately.
Ministries, government offices, courts, police, financial authorities and patent offices, right up to foreign policy institutions around the world work with a wide variety of highly sensitive data.
Theft, unnoticed alteration or disclosure of such data can have serious consequences for political processes and relations, for the economic development of a country, or for the confidence of citizens in its institutions.
For ministries and authorities
As a long-standing service provider for public institutions, Radar Cyber Security knows about the requirements and risks. Its holistic approach to cyber security identifies threats and risks at an early stage. The security monitoring process encompasses all systems and data traffic, along with access to sensitive systems and files. Other tools are also used, in addition to end point detection, to spot data transfers from internal to external IP addresses with which no business relationship exists. Log data from servers, network devices, and applications are also analyzed centrally and correlated with the findings of all modules. Big Data analytics and threat intelligence add an additional dimension to the comprehensive cyber security measures.
The Radar Risk Cockpit is where critical information from security monitoring and risk assessments are displayed so that immediate corrective action can be taken.
Authorities apply cyber security measures to protect the integrity of critical infrastructure in financial systems, healthcare, scientific and security institutions, defense, aviation, and intelligence-gathering.
Ransomware attacks such as Wannacry in 2017 not only affected logistics or telecommunications companies, but also led to serious disruptions in the healthcare sector, paralyzing many hospitals.
In the healthcare sector, IT security not only involves protecting patient information, but also ensuring the operation and use of important devices to avoid life-threatening disruptions. After all, apart from sensitive data that are stored, such as social security numbers, medical history, etc., emergencies need to be admitted and treated, and vital diagnostic equipment must continue to operate.
Healthcare facilities, like many other companies in the field of operational technology, have the same problem in that the devices in the network must be constantly available or in use, and therefore cannot be updated or patched.
Time for cyber fitness
As a result, networks and end devices must be protected accordingly to guarantee comprehensive protection. The approach taken to security in the healthcare sector as whole must become more proactive and forward-looking, which means that, in addition to network analysis, vulnerability management, and log files, the focus should also be on end-point security and, above all, on the knowledge of threat intelligence. All this know-how is actively used to improve security without ever compromising performance or operation.
Whether by rail or air, whether it involves a conductor, air traffic control system, or toll collection, digitization has arrived in the transport sector.
The transport sector consists of complex networks, large volumes of real-time data, and a multitude of integrated devices. Modern possibilities such as automation and networked vehicles that exchange information in real time with other networked vehicles and control systems in the environment are being used in the transport sector to improve both efficiency and safety. Yet at the same time, this makes all means of transport vulnerable to attack, which means that they must be protected against attacks, unauthorized access, damage, and manipulation.
Everything in motion
Dangers can come from inside or outside, which is why all aspects of IT and OT security must be covered – from ticket machines to office systems and large data centers. Not only the networked systems must be coordinated and orchestrated, but also the steps taken to improve security. While network analysis, vulnerability management, and log files are one aspect here, attention must also be paid to end-point security.
Both bricks-and-mortar retailers and e-commerce are extremely interesting targets. Countless transactions are carried out every day with customers or suppliers. Retail companies also hold sensitive and important customer data and store, among other things, e-mail and delivery addresses, as well as bank details.
Weaknesses in online shops, compromised scripts from third parties on payment pages, or inadequate database security are low-hanging fruits, presenting ways for attackers to gain access to customer payment information.
Greater customer security
The frequency and severity of cyber attacks also affects the retail industry. Companies and their brands live from the trust of their customers. Those who define risks and areas of attack at an early stage can proactively take steps to safeguard against them, protecting both the turnover and the company itself. Security also generates trust.