Supporting your in-house security operations
Materna Radar Cyber Security offers you full support for running your efficient and comprehensive security operations. Well proven cyber security processes are established at your organization. Your employees receive trainings and instructions with the necessary documentation.
Materna Radar Cyber Security provides support at all stages: from cyber security consulting to integration into your organization as well as continuous improvement measures.
For Managed Security Service Providers
If your company aims to offer cybersecurity services to your customers, our solution is the right choice. Materna Radar Cyber Security offers tailor-made solutions to become a provider of managed security services or integrate our services into your portfolio. Materna Radar Cyber Security works with proven and compliant technology.
Additionally a go-to-market experience in combination with trainings in terms of service architecture, service delivery as well as technical sales approaches is part of our offering.
Technology operated by Materna Radar Cyber Security
Regular updates, integrated threat intelligence and continuous improvements are included. Big Data is proceeded and analyzed, finally resulting in customized reports, alerts and a central source of information: the Risk & Security Cockpit.
The goal is maximum effectivity and efficiency regarding Detection & Response. Our experience is always available to you.
The platform to analyze and assess cyber threats
Our Platform stands for cutting-edge cyber detection technology. Our inhouse developed solution is characterized by state-of-the-art intelligence automation being used to comprehensively monitor IT security and perform IT risk assessments. The agnostic platform is able to analyze and evaluate any logs, networks and other kinds of information.
Process
- Risks are detected by means of a multi-level correlation approach, combining different information and events, both in an automated way and through work by experts. Both customer-specific analogies and analogies involving several customers and sectors are applied.
- This correlation is based on a wide range of events, originating from both IT itself and the environment in which IT systems are operated. For this purpose, intelligent event middleware is used.
- Risks are presented for different user groups, including those not involved in IT: based on needs and clearly arranged, for critical business processes, IT services, and legal and regulatory requirements.
The Detection Modules used in our Cyber Security Services lay the perfect foundation to safeguard your digital activities and footprints.
Your benefits using Radar Platform
Intelligent and efficient endpoint-to-endpoint solution
Extensive knowledge database
Turnkey concept to commence operations in a very short space of time
Scalable deployment to increase turnover
Secure throughout all phases
We support you during each and every phase: from planning and implementation through to integration into your organization and continuous improvement. Whether you want to build or expand a Security Operations Center, we provide the proven technology which is tailored to your needs. Correlation engines recognize and evaluate the data. Constant updates, integrated threat intelligence and continuous development are part of the technology.
We support through Empowerment Services: we tailor olutions to suit your needs, conduct training courses for your SOC team, and work with you to establish processes and best practices that fit into your organization.
Inhouse Cyber Defense Center
For Managed Security Services Providers
Full package of hardware & software, documentation & policies
Support from implementation through integration and improvement
Tailored to your needs through frequent updates, integrated Threat Intelligence and continuous improvements
Training of your CDC team through our highly qualified experts
For Managed Security Services Partners:
Sales trainings
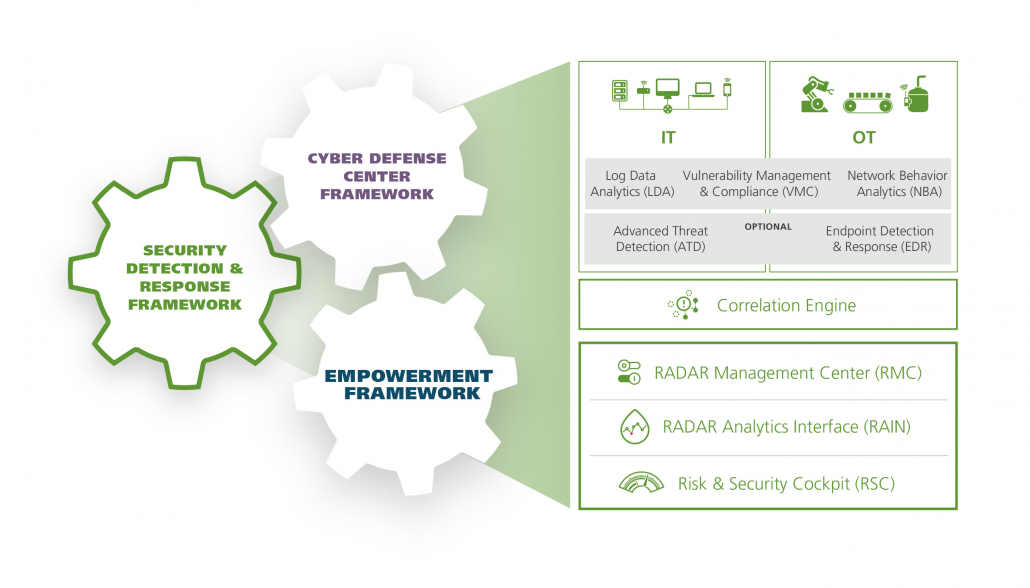
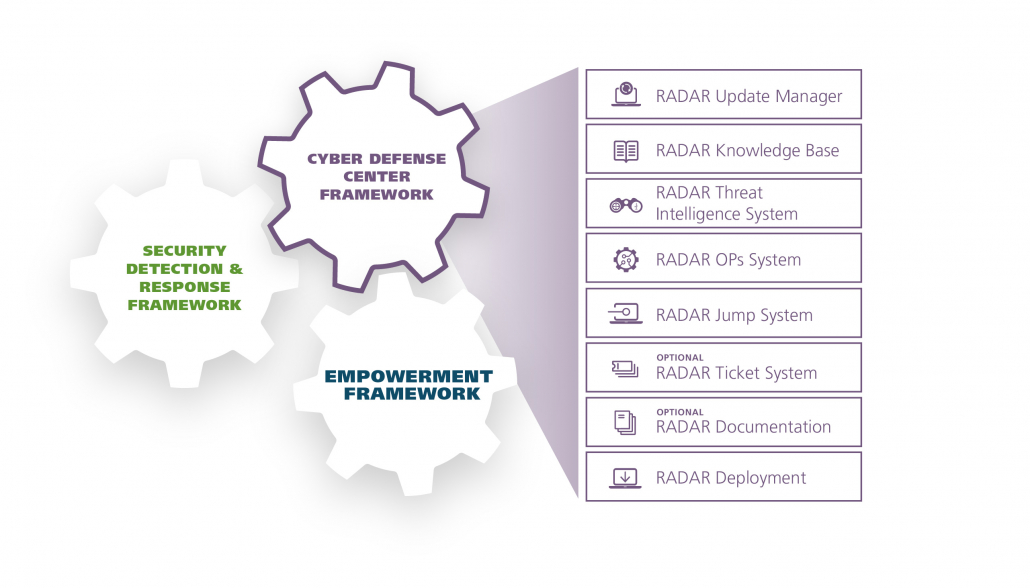
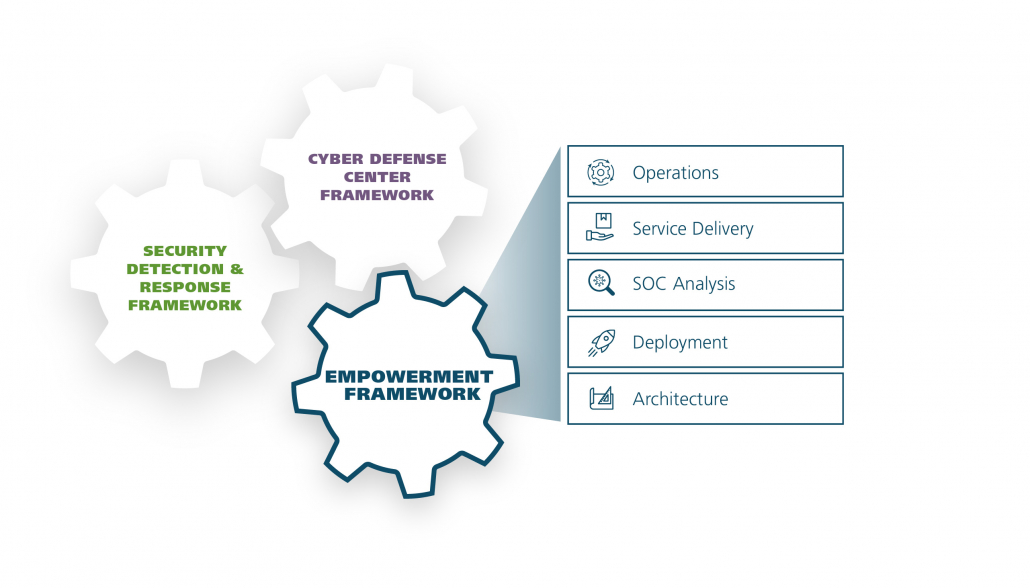
Cyber Defense Framework components
IT Security takes more than SIEM
Materna Radar Cyber Security works with a wide range of detection modules. Customers can pick their individual service components for their threat detection and cyber security strategy:
Log Data Analytics (LDA)
Log Data Analytics, also known as Security Information and Event Management (SIEM), comprehends the collection, analysis and correlation of logs from various sources, distributing alerts in case of security flaws or potential risks.
Network Behavior Analytics (NBA)
With Network Behavior Analytics we detect malware, anomalies and other risks in network traffic, deriving from signature and behavior-driven engines.
Vulnerability Management & Compliance (VMC)
Vulnerability Management and Compliance enables consistent internal and external vulnerability scans with comprehensive detection, compliance checks and coverage tests. As part of an integrated software compliance check, authorized/unauthorized software is determined for each server or server group using a set of rules and a continuous analysis pattern of the current status.
Advanced Threat Detection (ATD)
Advanced Cyber Threat Detection consists of sandbox technologies of the latest generation, that detect advanced malware throughout emails and downloads. Suspicious email traffic will be alarmed and flagged.
Endpoint Detection & Response (EDR)
Endpoint Detection and Response enables analysis, monitoring and detection of host anomalies, leading to active reactions and immediate alarms.
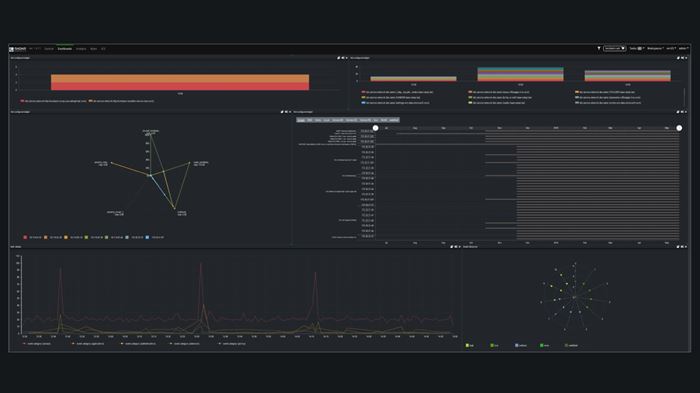
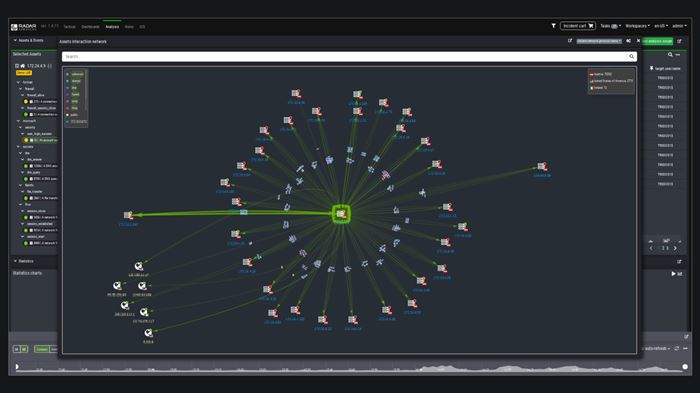
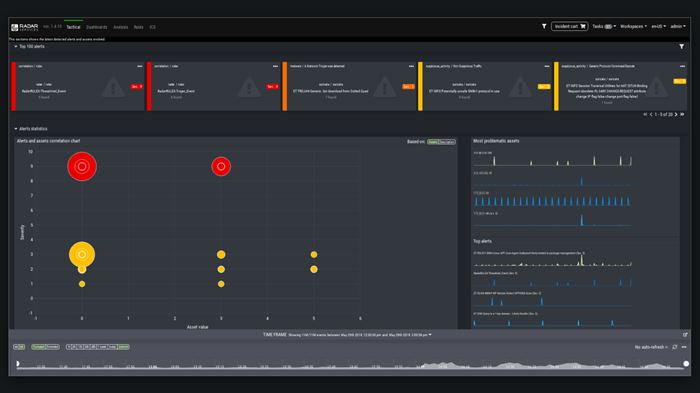
Complex data interpreted with simplicity
The Radar Analytics Interface (RAIN) is the latest generation of Materna Radar Cyber Security’s graphical user interface. Cyber security analysts can directly access all the data of the underlying systems, as well as use and visualize the data sets clearly. The data accumulates in a highly interactive, responsive analysis interface. Experts are enabled to search for threats from different perspectives. With RAIN, analysts can quickly connect to other useful data sets, such as vulnerability information, incidents from log data analytics and numerous logs. Comprehensive drill-down and correlation functionalities empower analysts to execute complex queries – supported by a graphical representation of the relationships between the elements. RAIN makes threat detection smarter and more effective.
The advantages
See the big picture and gain meaningful insights
Rapid and unprecedented threat detection
Minimize complexity
Extended workflow functionalities
Data visualization
View data in a global context
Comprehensive drill-down and correlation functionality
Customizable user interface and freedom to choose the perspective
Even smarter and more effective threat detection
Full integration into Materna Radar Cyber Security’s bundled portfolio