With the new EU-wide cyber security directive NIS2 entering into force, new regulations and security requirements are on the way. The first Europe-wide directive for a common level of cyber security (NIS) from 2016 has been extended by a few points in 2023. In the following, we explain which sectors are subject to this extended directive and what companies and authorities must do now.
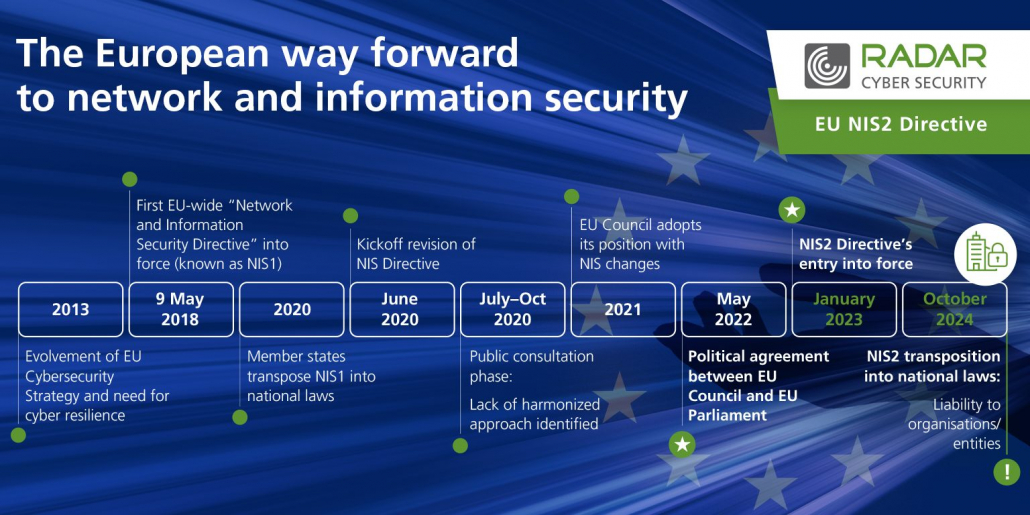
Increasing networking and digitization also mean that attackers are becoming increasingly sophisticated about digital targets. For a common level of cyber security within the EU, the NIS directive (Security of Network and Information Systems) was launched a few years ago. Due to the further increase in the threat situation in the digital space, the EU refined and expanded the directive at the beginning of the year. The directive aims to better protect critical sectors and infrastructures within the EU and to make them safer. In order to achieve this, it is necessary to tighten the security requirements for companies quickly and consistently, because the attackers are also constantly developing new strategies. Organizations that are subject to the directive, must act now, as the timeline stipulates that the requirements will be transposed into national law by autumn 2024 at the latest. But which companies are actually meant and what is required of them?
Additional sector
The NIS2 directive goes beyond its first version to include other sectors that are crucial for economies and societies. These include providers of public electronic communications networks and services, data centre services, waste management, manufacturing of critical products, postal and courier services, and public administration entities. Moreover certain areas of the health sector and research are also subject to the directive, for example when it comes to the development and manufacture of medicines. The critical sectors increase to seven. The major sectors grow to eleven. In the meantime, 18 different sectors are part of the critical infrastructure. The directive applies to all companies in critical and major sectors with 50 or more employees as well as EUR 10M in turnover. Some operators, for example of digital infrastructure or public administration, are to be regulated regardless of size. They are all subject to the specified standard. In the case of smaller companies belonging to one of the sectors, there is a margin of discretion. They are bound to certain cyber security obligations.
Learn more and subscribe
The next steps
Member States have to transpose the NIS2 directive into national laws until October 2024. During this period, Member States are obliged to adopt and publish the measures to comply with the directive. In Germany, the IT Security Act 2.0 of 2021 has already anticipated some changes, such as the expansion of the sectors, of NIS2. However, other precautions, such as affecting medium-sized and large companies and certain measures, are still missing and will have to be implemented in 2023 by means of an amending law or ordinance.
NIS2 will therefore lead to a significant expansion of affected institutions and its transfer into German law (IT Security Act), opens up a new scope for action in order to protect critical infrastructure comprehensively. A unified cyber security standard within the EU requires combined forces of companies, authorities and security specialists who work closely together beyond national borders.
Tightened security requirements
What security requirements does the EU-wide directive have for companies and authorities? Again, the second version of the directive goes beyond the first. The NIS2 directive tightens the requirements for cyber security risk management, which companies are obliged to comply with. Organizations must take technical, operational, and organizational measures to manage cyber security risks and minimize the impact of potential incidents. In order to be able to meet this requirement, NIS2 provides for concrete, targeted measures, such as guidelines for risks and information security, establishment of incident management, authentication measures, training for employees, specifications for encryption or emergency communication. The safeguarding of the entire supply chain up to the secure development of suppliers has also been added.